- Part 1: Why we built the Shield
- Part 2: WordPress Super Admin Protection
- Part 3: WordPress Firewall Feature
- Part 4: WordPress Login and Brute Force Hacking Protection
- Part 5: The WordPress Comment SPAM Killer
- Part 6: WordPress Automatic Updates Management
Shield has some of the most effective WordPress login-security protection available.
It blocks all brute force WordPress login attempts using simple, non-intrusive techniques; it also ensures that the identities of all logged-in users have been verified.
There is no other plugin available, either free or paid, that has login protection to this degree.
In this article I’ll explain how we do it, why it is works so well and the options you should enable.
What does the WordPress Login Guard feature protect against?
Broadly speaking, the WordPress Login Guard feature has 2 main components:
- User Identity Verification – i.e. you are always who you say you are
- Brute Force Login Protection – i.e. no more account hacking
We’ll outline each of these below with full details of the options available.
User Identity Verification with Multi-Factor User Authentication
As explained here, multi-factor authentication ensures that the user attempting a WordPress is verified as the legitimate user. Shield primarily uses email as the basis for this verification.
It offers 4 methods of two-factor authentication which can be used together to form multi-factor authentication.
- Google Authenticator
- Yubikey
- Passkeys/WebAuthn
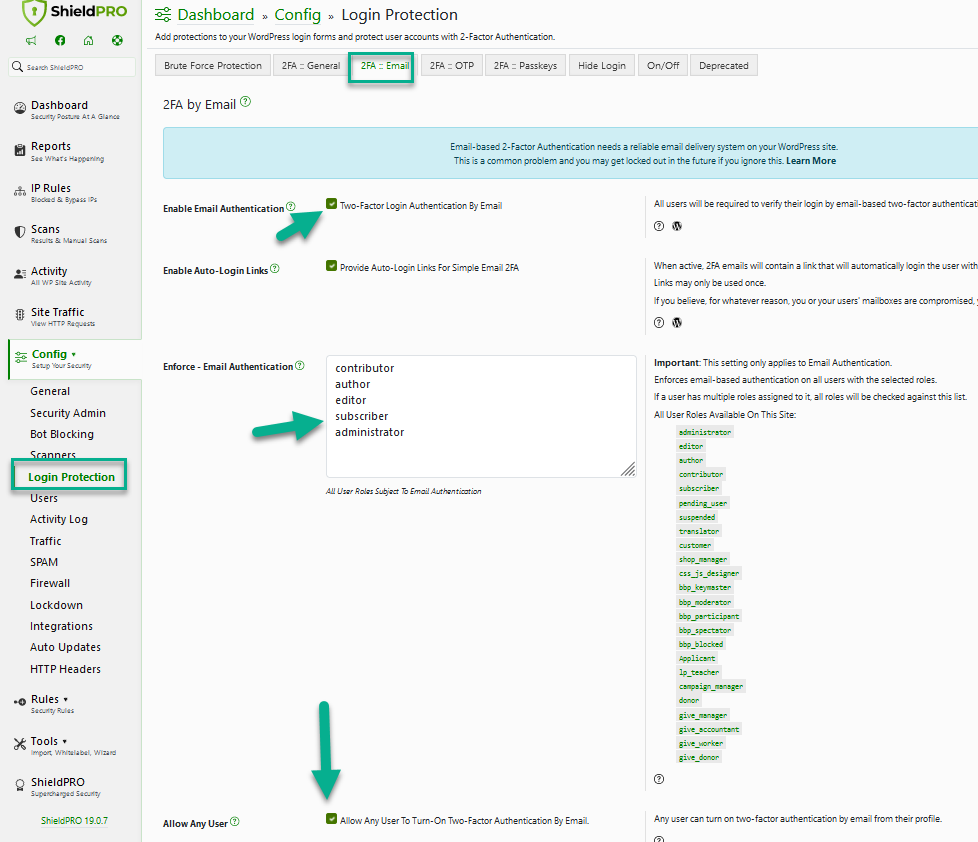
Email-Based Two-Factor Authentication
Email – based 2FA is one of the best ways to secure account access – for any platform, WordPress included.
When verified by 2FA login code, every time a page loads the plugin will check the logged-in user against the location at the time of verification. This means that a verified user can use this 2FA method from 1 single location only.
For example, you can login with the same username using Firefox and Chrome on the same computer, but you will have to verify your identity twice, since the location isn’t the same.
When you enable this feature in Shield, you can either
- Enforce email-based 2FA on all users or specific roles; or
- allow any user to turn it on from their profile.
You also have the ability to use Auto-Login Links option.
When active, 2FA emails will contain a link that will automatically login the user without the need to enter 2FA Codes.
Google Authentication Two-Factor Authentication
When enabled, you will have the option to add Google Authenticator to your WordPress user profile.
Note: Google Authenticator, LastPass Authenticator & Microsoft Authenticator are all supported by this option, but it is referred to as Google Authenticator for simplicity.
Yubikey-Based Two-Factor Authentication
Yubikey is a hardware-based, two-factor authentication system. It provides a completely independent verification system that is not connected to either email addresses or user accounts of any kind.
They let you create one-time passwords (OTP) that are then verified against the Yubikey web service at the time of WordPress login.
We recommend Yubikeys as a highly effective, and cost-efficient authentication system, and have also implemented it for the iControlWP WordPress Management system.
Yubikey Unique Keys and WordPress Users
Before the Yubikey authentication can be used, you must create a Yubikey App and API key. Explanation on how to do that can be found here.
Once this is done, you can begin assigning WordPress username to the Yubikeys themselves. This done, as show in the screenshot, by comma-separating a WordPress username with the unique 12 digit Yubikey IDs.
Yubikey IDs are simply the first 12 digits of any Yubikey OTP, and you may assigned multiple Yubikey IDs to the same user simply by taking a new line and repeating the username with the alternative ID.
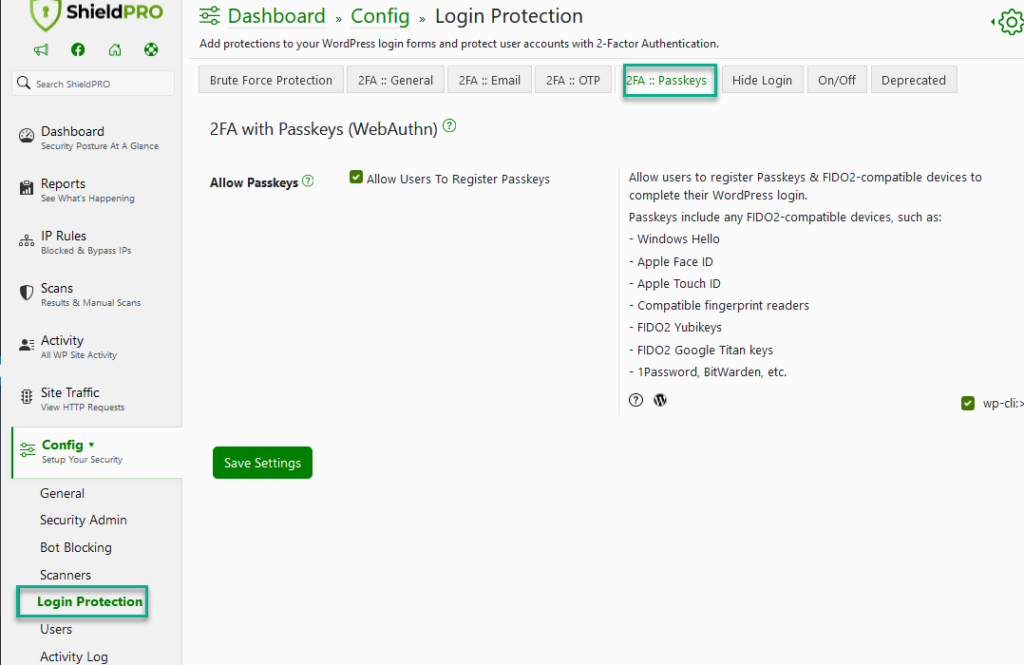
Passkeys/WebAuthn
Passkeys/WebAuthn is an open standard for simplifying 2FA. You may already have a login device, such as Yubikey, or Google Titan Security Key. If you don’t have one, we highly recommend getting at least 1 of them.
Passkeys let you verify your login/identity using 2-factor authentication.
To allow users to use Passkeys to complete their login, simply go to the Login Guard module of the Shield plugin > 2FA: Passkeys and enable this feature.
Once you’ve done this, you’ll see a button in your WordPress user profile to register a new Passkey(s).
Click this button and the registration process will begin.
There is more information on this here.
Brute Force Hacking Protection
Our Approach To Brute Force Login Protection Explained
In the last few years there have been a number of reports of brute force login attacks against WordPress websites. This is because the WordPress platform is now so prevalent, that building a system to attack WordPress makes much more sense if more hacking success is desired.
The Shield plugin blocks and limits brute force login attempts using 4 separate and highly effective techniques:
- two-factor authentication – there’s no way for a bot to know it’s successfully logged in if there are 2 authentication stages.
- login cool-down system – probably the most powerful system for brute force login prevention. It works by completely blocking login to a site until a given number seconds have passed since the previous attempt.
- AntiBot Detection Engine – completely removes the need for annoying WordPress login form CAPTCHAs, and GASP “I’m a human” checkbox.
Except for two-factor authentication, you’ll find none of these approaches uses the database to store IP address lists for blocking. IP addresses don’t matter and should not be used as the foundation of a WordPress security policy.
Read that again, because you’re probably so conditioned to think of IP blocking etc. that you believe this without even thinking about it.
Furthermore, if your website is being attacked by a distributed (meaning thousands of IP addresses) system of bots, blocking login attempts based on IP address is utterly futile, and only adds load to your server because of all the database writing and look-ups.
With Shield development, we took a step back, thought about the nature of the most recent attacks on WordPress. We discovered that IP addresses are not a sound foundation upon which protection should be designed.
That said however, we do use the connecting address as the basis for identifying verified users. But this is completely different since their IP address isn’t used to block, but rather accept and match a user session to a verified identity.
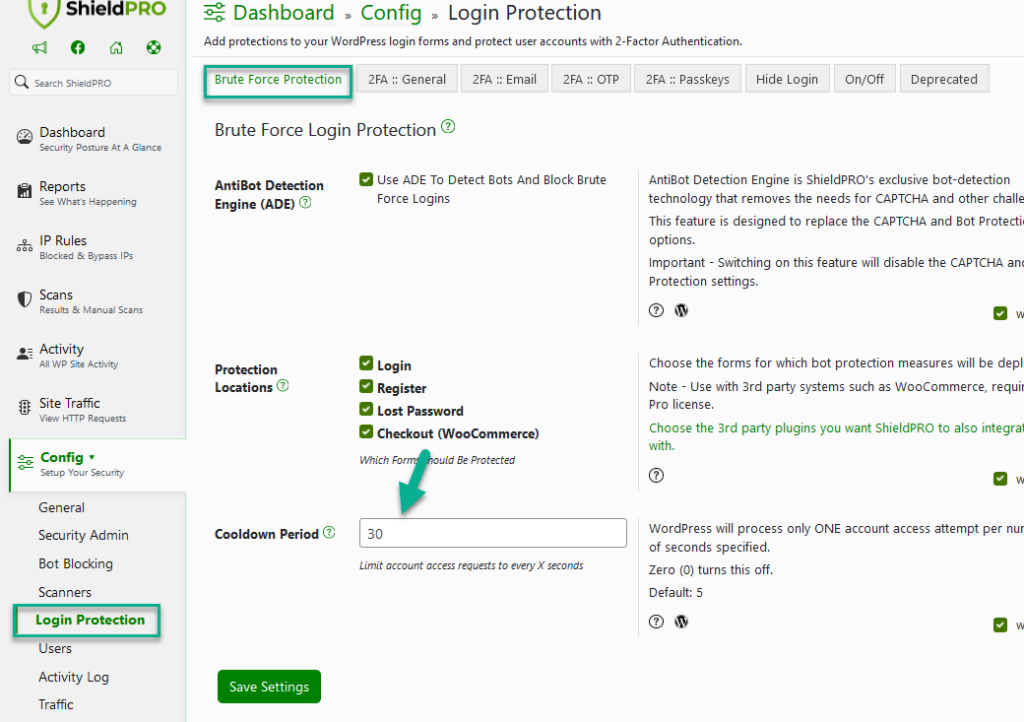
There are 2 options available dedicated to preventing brute force hacking the login on your WordPress sites, and we recommend you enable all of them unless for whatever reason they interfere with how you use your site.
Option: WordPress Login Cool Down
This feature alone should be enough to block all brute force login attempts.
The value you decide on here represents the time, in seconds, that WordPress will be forced to wait before processing any other login attempt after the previous attempt.
Option: Login Cooldown
Without a cool-down feature, bots connecting from anywhere can try and authenticate with your site as much and as often as they can. Let’s take an example…
Say a bot tries 10 times a second without overloading your server:
- In 1 minute, that’s 600 attempts.
- In 1 hour, that’s 36000 attempts.
- In 1 day, that’s 864000.
- It takes 1.15 days to make a million requests to your site at that rate.
Instead, if you put a minimum of 5 seconds between login attempts, it would take nearly 60 days to perform a million requests. Way better! And it gets better the longer you make your cool-down period.
And, it doesn’t use the database to store attempts and counts etc., or care about IP addresses, or anything like that. It’s very efficient!
Apart from the Shield’s Login Cool Down feature, there’s another powerful way to put a stop to bots and visitors that abuse your website and your hosting resources. It’s called Traffic Rate Limiting protection for WordPress. This is where you restrict the number of requests a single visitor can make against your site, within a certain period of time.
Option: AntiBot Detection Engine (ADE)
ADE is used to detect Bots and block Brute Force logins.
It’s ShieldPRO’s exclusive bot-detection technology that removes the needs for CAPTCHA and other challenges.
We go into further details on this here.
Shield security offers High Grade Login Protection
As you can see from the explanation of these options, the Shield plugin offers extremely effective protection against WordPress login attacks, and provides tried and tested methods for verifying the identity of users active on the system.
We’ve chosen to take a fresh approach to solving WordPress brute force hacking attempts, rather than follow the herd and create a copy-cat security system that adds weight and load to your already burdened WordPress system.
We’re always open to feedback about new ways to improve our Login Protection and two-factor authentication options, so please leave a comment below if you have ideas or suggestions for us.
Hello dear reader!
If you want to level-up your WordPress security with ShieldPRO, click to get started today. (risk-free, with our no-quibble 14-day satisfaction promise!)
You'll get all PRO features, including AI Malware Scanning, WP Config File Protection, Plugin and Theme File Guard, import/export, exclusive customer support, and much, much more.
We'd be honoured to have you as a member, and look forward to serving you during your journey towards powerful, WordPress security.




Hi,
how do you ensure to not lock out yourself with the Login Cool Down system while some bots are tampering the login page?
Are you also protecting the xmlrpc.php in any way?
There’s nothing you can do about that unfortunately if the bots are cracking away at your page. Most bots would get blocked by the automatic blacklist if they’re repeatedly hitting you with this.
As to XML-RPC, we have a couple of options ranging from by-passing the login/user sessions systems to completely disabling it:
https://www.icontrolwp.com/2015/10/automatically-block-brute-force-amplification-attacks-against-wordpress-xmlrpc/
I am hitting “You must check that box to say you’re not a bot.”.
However the check box is not present in the login screen.
This will happen if you’re using custom login form that doesn’t honour/fire standard WordPress login hooks/filters.
Hi, my blogs have been undergoing a series of heavy brute force attacks as what the host said. I have Wordfence and Shield installed. Would Shield clash with Wordfence? With the two installed, I am still experiencing very heavy attacks that kept bringing down the whole server over the past 1-2 weeks. And it happened again last night and the night before. It seemed to come very fast and furious. I was very puzzled as I have used Shield to change the default /wp-login.php page to /xxxx using Shield and yet I was still getting report from Wordfence of people trying to access it. Your post is enlightening … at least now I know an attacker doesn’t have to be at my site url/wp-login.php to login. Please kindly advice what I can do as I am at a lost here. Thank you.
Hi,
Wouldn’t the login cool down feature interfere with users logging into a high-traffic website like an e-commerce site?
Hi Adrian,
Yes, this could certainly interfere with high traffic websites. It really depends on the scenario, since authentication is only a small part of a user activity on a site, then the likelihood of collision for legitimate users is small.
However, you can fully adjust the interval of the cooldown. The smaller the interval, then less likely there will be a problem. So even selecting as low as 1 second will make a significant difference.
If you want to ensure there is no interference, disable the option entirely by setting it to zero (0).
Thanks!